Modern businesses rely on secure and scalable infrastructures to handle their growing digital demands. Kubernetes, a powerful container orchestration tool, has become the go-to choice for deploying and managing applications. In scenarios where security is paramount, incorporating DMZ (Demilitarized Zone) clusters into Kubernetes deployments offers a robust solution. This guide explores the intricacies of Kubernetes deployments with DMZ clusters, their benefits, and how to implement them effectively.
What Are DMZ Clusters?
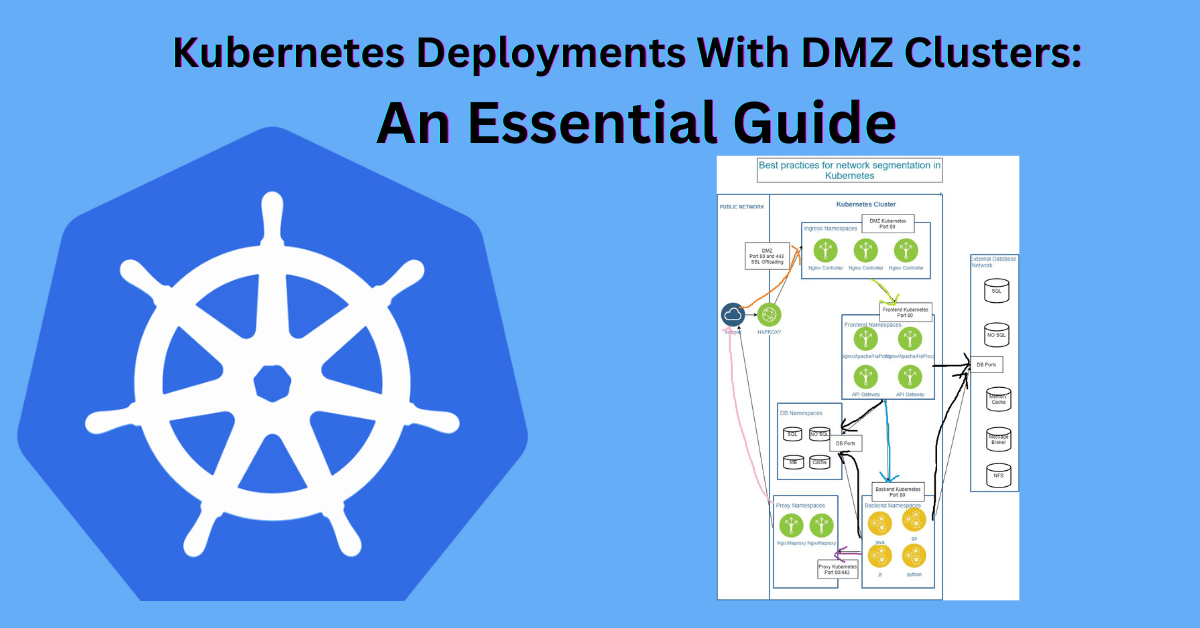
A DMZ cluster acts as a buffer zone between the internet and an organization’s internal network. It provides an additional layer of security, ensuring that only authorized traffic can access sensitive internal resources. When combined with Kubernetes, DMZ clusters enable organizations to run applications securely while maintaining high availability and performance.
Why Use DMZ Clusters in Kubernetes Deployments?
- Enhanced Security: By isolating critical components from direct internet access, DMZ clusters reduce the risk of cyberattacks.
- Improved Compliance: Many industries require stringent data security measures. Using DMZ clusters can help meet regulatory requirements.
- Traffic Control: DMZ clusters provide granular control over incoming and outgoing traffic, allowing for better application monitoring and management.
- Scalability and Flexibility: Kubernetes seamlessly integrates with DMZ clusters, enabling secure scaling of applications.
- Mitigation of Threats: By establishing a barrier between external and internal networks, DMZ clusters help mitigate the risks of DDoS attacks and other malicious activities.
Key Components of Kubernetes Deployments With DMZ Clusters
To successfully deploy Kubernetes with DMZ clusters, it’s essential to understand the critical
components:
- Ingress Controllers:
- Manage external access to services within the cluster.
- Ensure secure communication using SSL/TLS protocols.
- Network Policies:
- Define rules to control traffic between pods, namespaces, and external entities.
- Prevent unauthorized access by specifying ingress and egress rules.
- Load Balancers:
- Distribute incoming traffic across multiple pods to ensure availability and performance.
- Firewalls:
- Protect the DMZ cluster by allowing only approved traffic through defined rules.
- Service Mesh:
- Enhance security with encrypted communication between services.
- Simplify traffic management and observability.
- Monitoring Tools:
- Tools like Prometheus and Grafana are vital for real-time monitoring and tracking of traffic flows.
Setting Up Kubernetes Deployments With DMZ Clusters
Implementing a DMZ Cluster in Kubernetes
Here’s a step-by-step guide to setting up a DMZ cluster in Kubernetes:
Step 1: Plan the Architecture
Design a multi-cluster environment with:
- A DMZ cluster for public-facing services.
- An internal cluster for private workloads.
Step 2: Deploy the DMZ Cluster
- Set up the cluster: Use Kubernetes deployment tools like ClusterAPI or managed Kubernetes services (e.g., GKE, EKS, AKS).
- Configure ingress: Deploy an ingress controller to handle traffic.
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
name: dmz-ingress
spec:
rules:
- host: public-service.example.com
http:
paths:
- path: /
pathType: Prefix
backend:
service:
name: public-service
port:
number: 80
Step 3: Enforce Network Policies
Restrict traffic between DMZ and internal clusters:
apiVersion: networking.k8s.io/v1
kind: NetworkPolicy
metadata:
name: limit-dmz-access
namespace: dmz
spec:
podSelector:
matchLabels:
app: public-service
ingress:
- from:
- ipBlock:
cidr: 0.0.0.0/0
ports:
- protocol: TCP
port: 80
Step 4: Secure Communication With Service Mesh
- Deploy a service mesh like Istio to secure traffic between DMZ and internal clusters.
- Encrypt all communications using mutual TLS (mTLS).
- Define traffic policies to restrict access.
Step 5: Monitor and Audit
- Use tools like Prometheus and Grafana to track traffic patterns.
- Log cluster activity using ELK stack (Elasticsearch, Logstash, Kibana).
Step 6: Monitor and Audit Traffic
Set up monitoring tools like Prometheus and Grafana to track traffic patterns and identify anomalies. Regularly audit firewall rules and network policies to ensure compliance with security standards.
Best Practices for Kubernetes Deployments With DMZ Clusters
- Segmentation: Clearly segment workloads between DMZ and internal clusters to prevent lateral movement during a security breach.
- Regular Updates: Keep Kubernetes and associated tools up to date to mitigate vulnerabilities.
- Access Control: Implement role-based access control (RBAC) to restrict access to the cluster.
- Data Encryption: Use encryption for data in transit and at rest to protect sensitive information.
- Disaster Recovery: Have a robust backup and recovery plan to restore services in case of a failure.
- Proactive Testing: Conduct regular penetration testing and vulnerability assessments to identify and address potential weaknesses.
Challenges in Implementing DMZ Clusters
While the benefits are significant, setting up Kubernetes with DMZ clusters can be challenging:
- Complex Configuration: Requires expertise in network security and Kubernetes.
- Higher Costs: Additional infrastructure and tools may increase expenses.
- Performance Overhead: Extra layers of security can introduce latency.
- Maintenance Demands: Managing a DMZ setup requires continuous monitoring and updates to stay effective against evolving threats.
Conclusion
Kubernetes deployments with DMZ clusters provide a robust security architecture for modern applications. By following the best practices and patterns outlined in this guide, organizations can build secure, scalable, and maintainable Kubernetes environments. For more detailed guides on Kubernetes security and cloud-native technologies, visit our security best practices section and explore our comprehensive resources.
Remember that implementing DMZ clusters in Kubernetes deployments requires careful planning and ongoing maintenance. Regular security assessments and updates ensure your architecture remains robust and efficient.
For a deeper dive into Kubernetes and related technologies, check out TechTalksToday. This resource provides valuable insights into modern tech solutions.